Well in light of the recent fascination and media-hype about spam from a new range of devices dubbed, the “Internet of Things” I thought I post some information.
The media-hype is a little surprising in some ways as this ‘hack’ is old news, old technology and has been happening for years. I first identified and tested for it publicly with the Spam and Open Relay Blocking System’s (SORBS) automated proxy tester. The only thing that is different is now is the devices that can be exploited. It used to be home routers, and computers directly connected to the Internet, but now it’s phones (Smart, VOIP and others), it’s Televisions, it’s Fridges, Cameras (usually security cameras, but not always), Digital Video Recorders, Set-Top boxes (Satellite receives, cable receivers, and Media Players etc), Audio Amplifiers, and many many more…
It was published by Proofpoint that ‘Thingbots” are sending spam. Unfortunately it was taken by the media that “Thingbots” are the resulting robots from someone breaking into these devices and installing some software that sends spam, in a similar way that hackers try to trick people to download malicious software to their computers and laptops. Whilst this is possible and undoubtably will happen in the near future, this is completely wrong at the present time. Thingbots is a reference to the device being and ‘thing’ and being commanded to do something other than it’s designed purpose, regardless as to what that device or it’s purpose is.
For example, a ‘smart fridge’ is designed to keep food cool, keep track of the contents and alert the owner (maybe by email) if there is a problem with the fridge itself or with some of the contents (eg, like there being no milk left.) The fridge is not designed evade security/anti-spam systems and to proxy or relay emails to a third party, but is is currently possible via a variety of devices. How, you might ask, well I’ll get into that below, but first you might be asking why are these devices even connected to the internet? Well it’s because people do not have a clue from a security perspective. Neither the people that own the device nor (in a lot of cases) the designers. The manufacturers are embedding computers into the devices and as a home appliance manufacturer (whether it be a fridge, a TV or other device) they are not experienced in IT Security, its not their job (yet) to be concerned with security, they want the functionality at the cheapest price. To this end, they get people in their IT developer section (if they even have one, some just ask another supplier to provide them with the embedded software) straight from University, or school, with one very experienced manager most of which have no idea about security of the devices but they can code…. Worse, they make fatal management decisions giving the commands.. “Make it work! Make it work quickly. Make it work cheaply!” When they have a developer that says, “Hey, what about security?” the answer comes back, don’t worry about it, it’s in the home, it’s safe behind the owners’ firewall, or “well put a password on it!”.. and so it begins..
Why this is bad..
Seems like a no brainer, the device is behind a firewall, it’s being NAT’d (Network Address Translation) so it’s not available on the Internet.. or is it?
Well most of these devices are running one of two Operating Systems, Windows or Linux, both operating system types have embedded versions, ‘Embedded Windows’ for Windows, or ‘BusyBox’ for Linux (amongst others, but that seems the most common.)
I’m not going to mention Embedded Windows here at all as I know nothing about it, and to be honest, at the moment, I don’t want to… personal prejudice and all that..
Now in the case of Linux, the kernel itself is mostly secure and requires detailed and specialised knowledge to break into in the later versions. The problem is they kernel is just part of the OS. Linux is a UNIX variant and as such it relies on many applications as part of the OS for configuration, testing and usability. In the case of BusyBox these applications are often special versions that are cut down and trimmed as much as possible to save on space as embedded devices are usually limited on available memory, and they are all rolled into the same executable that operates as a multi-purpose tool “The Swiss Army knife of Embedded Linux” (it is given multiple names but only stored once in memory, and depending on the name you use to execute it, will depend on what function it performs.) This is great, it makes devices very easy to build and makes it very versatile, for example, the Patriot Box Office, AC Ryan, Masscool and CinemaTube media players all run on the Realtek RTD1073 chipset BusyBox and a Linux kernel is an ideal OS for the device.. However, they are yet another example of the Internet of Things.. and in the case of the Masscool device a particularly good example of whats wrong…
My Masscool Media player…
I bought it in 2010 as it was one of the first HD capable media players that I could find with a good review, it also was one of the only ones with a HDMI port on the back.. Very quickly I found that it wouldn’t play some of the updated media formats so I went looking for firmware updates. Non available, I relegated the box to the junk pile for a couple of years… Recently I set up my games room and thought I’d get it out again and see if I could hack it to work with Plex as this is an XMBC fork that works well as a Media Server and has a DNLA server built in and the DNLA server can be hacked to transcode to various formats.
My first job was to see if I could get a firmware update, and went looking again. What I found was two things, first, Masscool had not released a single update to the media player and in fact had stopped producing any Media Players. Second, there is a sub-culture around the Patriot Box Office media players and firmware updates, and on the forums I found someone had posted the PBO unit was the same Chipset and board layout as a Masscool device. So I found a PBO firmware on their official site, downloaded it and started the firmware update to install it.. 30 seconds later I was told it was not made for this device and the update was aborted. After this, the unit was a ‘brick’ .. it had killed it. It could have been the boot code, it could have been something else.. don’t know but to many it would be dead and useless junk now, to me it was an opportunity to play. I had no concerns about ‘bricking it’ as it was already bricked so I looked for hardware modifications and found with an old mobile phone sync cable I could interact with the Realtek chip directly and as such I could load just about any firmware I wanted on it. The box within a few minutes was back operating in a really nice version of the Patriot Box Office software and playing all those newer media formats that I wanted to get in the first place. Of course having “hacked” it I suddenly had all the details of what it’s running and how it could be easily attacked. I had the default passwords, it was already listening for Telnet connections but I had been unable to get the information to logon to it until I hacked it… So I logged on and found that the Busybox installation had been complied with the ‘telnet’ option and therefore it is a device that can be a “ThingBot”.
More on how to exploit later…
My Dreambox DM500HD…
At home I have two Dreamboxes, a DM500HD and a DM800. both running ‘Enigma 2’, running OpenPLi 3.0 and OpenPLi 2.1 respectively… Running on an IBM STBx25xx Digital Set-Top Box Integrated Controller, and a 400 MHz Broadcom 7400 respectively. Enigma 2 is another Busybox embedded device, however is significantly different from other media devices as it is being actively developed, supported, upgraded and patched. All being said, by default DreamBoxes and the VU Plus, VU Duo devices and any other ‘Enigma 2’ device have a default password, login and open telnet port, in the case of Dreambox devices it is ‘root’ with a password of ‘dreambox’. Worse, not only does it have telnet built in, it also has a web interface which by default is NOT password protected and allows you to get to all the system settings, including login security options and files with passwords…!
Further as this is a ‘feature rich’ device with whole store full of plugins and applications most of which are written in Python which is also embedded in the OS as an application. This device is definitely a ‘ThingBot’, and it would be very easy to create a ‘Bot’ application that could be installed used to do a variety of other things – including compromise other devices.
So why would it be on the Internet? Well simple (and in fact I put mine on the Internet) you can watch TV from anywhere in the world using the webinterface and if you had an Andriod or iOS based smart phone or tablet you can download an application to give you TV on the device anywhere in the world.. (and it works very well with Apple iPads, I use it when I visit the USA as all 600 channels over there seem to be full of rubbish and it works well on the hotel wireless!)
My D-Link DNS-325 Disk Arrays (Home NAS devices)…
I have two at home, one has two 2T drives, the other has two 3T drives, one is a backup for the other and is mass storage for me, it’s based on the 1.2 GHz Marvell® 88F6281 (Kirkwood) chipset.. I moved all my Music from my Macs to there, I moved all my Movies there, I moved all my photos there… and they are both full, so I bought a new Netgear this Christmas (more on that below.) Now these devices are also Busybox based… what a surprise you may say.. no windows so far.. well that’s because I don’t buy windows anything, so this is all going to be something Linux based and mostly Busybox.. so anyhow, plugins available for it, eg, you can put a Database server (MySQL) on it, you can run a blog server on it, and of course you can put custom plugins on it by putting them in the root of the shared drive and rebooting it.. or using the web-interface. This includes adding an SSH server.. but why bother? It has a telnet server built in, and you don’t even need to use a username and password (in fact you can’t even set it to have a username and password unless you are quite technical as any changes are automatically lost when you reboot as the password has to be saved to the boot flash and it is not using the provided tools.)
Again once you’re in you can telnet out elsewhere..
My Netgear RN10400 NAS…
Built on the Marvell® Armada 370 1.2GHz chipset, it is also Linux though this is built on Debian Linux 7.1 (ReadyNAS version 6.x firmware) and unlike the others it’s secure(ish) by default. You have to turn on shell access via the web-interface before you can get access to the shell. However, unlike the others it has an extensive online plugin ‘store’ and you can install everything from a RADIUS server to a MySQL database server (by default with no credentials for root access) to your own blog and website. However, like the Engima 2 systems it is also extensively supported by the manufacturer and community so firmware patches are forthcoming on a regular basis.
Would this be on the Internet, well yes, many of the applications are designed to give simple ‘SOHO’ services at low cost, so it is very likely this device will be placed on the Internet, either directly or by using the ‘DMZ’ or ‘Port Forward’ capabilities of most home routers. Being a linux server under the hood, and not just a Busybox embedded device it also runs most if not all software that will run on a Debian Linux PC.. in fact it can even compile and run third party software that does not have packages capable of being installed on the NAS.
My Yamaha RX-A1030 A/V Receiver…
My latest toy, and very impressive one at that.. complete with it’s own gigabit network interface on the back. As I only got it a month ago I haven’t had time to poke around with it above look at the web-interface, port-scan it, and install the ‘Tablet’ remote control application. What I found was as follows:
michelle$ nmap -p1-65535 10.10.0.70
Starting Nmap 6.40 ( http://nmap.org ) at 2014-01-21 13:07 CET
Nmap scan report for 10.10.0.70
Host is up (0.0030s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE
80/tcp open http
1040/tcp open netsaint
1900/tcp open upnp
8080/tcp open http-proxy
10200/tcp open unknown
50000/tcp open ibm-db2Nmap done: 1 IP address (1 host up) scanned in 11.06 seconds
michelle$
Whoopsie! More on that a little later, but I can tell you it has an iTunes streaming service , as well as ‘Net Radio’ and AirPlay. (The important one to note here is the UPnP port.. more below)
My Thomson ‘Smart’ TV…
Another new addition (I got it at the same time as the Yamaha) and have not yet poked around with it, but it has it’s own App Store and Web Browser.. which is Embedded Opera and when you hit a webpage, with Flash content, it automatically attempts to download the flash plugin.. Do I really need to mention all the Flash vulnerabilities recently? As for the scan it only has port 13000 open, which I have no idea about yet except it isn’t as webservice.
My LG Smart TV…
Another device (and one I haven’t poked around with) except I know it is embedded Linux and has various plugins available, including the Plex media client which historically has been written in Python. LG have had a bad rap with their Smart TVs because of the fact they have been caught ‘calling home’, however like the Thomson and most other Smart TVs it is running embedded Linux.
So what about it…?
Well enough of the list of ‘ThingBots’ or devices that could be made to be ThingBots (Not even going to go into what on the LG Blu-Ray player and Melita HD Cable Set-top box – both Linux based).. As you can see many of these devices are running an OS that is available in the mainstream and therefore compilers, software and plugins are available. Some are securely setup by default, but most are not.
Some of these devices you can expect to see put on the Internet with out a security by the naive or experimenter, others you would not.. Or would you?
You see one of the problems with many of these devices is they all want to get access to the Internet, and even if you don’t give them access most of them are equipped to get access without you needing to know how. Most people barely know how to setup a home router, so there is no way they would be able to configure port forwarding if needed, and certainly they would not know how to do that securely for protocols such as H.323 (video conferencing protocol that also used in MSN Messenger for example) so to get around this back in the late 1990s developers came up with UPnP aka Universal Plug and Play.
UPnP (Universal Plug and Play)…
This protocol/software is built into most routers, home-firewalls and devices. It is a set of networking protocols that permits networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points and mobile devices to seamlessly discover each other’s presence on the network and establish functional network services for data sharing, communications, and entertainment. UPnP is intended primarily for residential networks without enterprise-class devices.
The UPnP technology is promoted by the UPnP Forum. The UPnP Forum is a computer industry initiative to enable simple and robust connectivity to stand-alone devices and personal computers from many different vendors. The Forum consists of over eight hundred vendors involved in everything from consumer electronics to network computing.
The concept of UPnP is an extension of plug-and-play, a technology for dynamically attaching devices directly to a computer, although UPnP is not directly related to the earlier plug-and-play technology. UPnP devices are “plug-and-play” in that when connected to a network they automatically establish working configurations with other devices.
The UPnP architecture allows device-to-device networking of personal computers, networked home appliances, consumer electronics devices and wireless devices. It is a distributed, open architecture protocol based on established standards such as the Internet Protocol Suite (TCP/IP), HTTP, XML, and SOAP. UPnP control points are devices which use UPnP protocols to control UPnP devices.
The UPnP architecture supports zero configuration networking. A UPnP compatible device from any vendor can dynamically join a network, obtain an IP address, announce its name, convey its capabilities upon request, and learn about the presence and capabilities of other devices. Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) servers are optional and are only used if they are available on the network. Devices can disconnect from the network automatically without leaving state information.
UPnP was published as a 73-part international standard, ISO/IEC 29341, in December, 2008.
What does this mean? well simply a UPnP device can tell the UPnP enabled firewall or router can open the ports without your knowledge – WITHOUT ANY AUTHENTICATION!
This is why back in 2002, Juniper Networks issued the following statement about their lack of support for UPnP in their devices:
SUMMARY:
Support for Universal Plug and Play (UPnP)PROBLEM OR GOAL:
Universal Plug and Play Some chat programs are UPnP awareSOLUTION:
NetScreen investigated UPnP, and have decided not to embrace this technology (as of mid 2002). Several factors went into this decision: a compromised host (say, with a trojan) could open the firewall entirely and permit other attacks and intrusions; all of the UPnP specs indicated that it is designed for the residential environment which is not NetScreen’s target market.
So how do they do it?
Follows is a series of images that show how it can be done. I will *not* be showing how to manipulate a UPnP firewall remotely, I will also not be doing this remotely as my network is secure against things like UPnP especially as my border is protected with a Juniper SSG520.
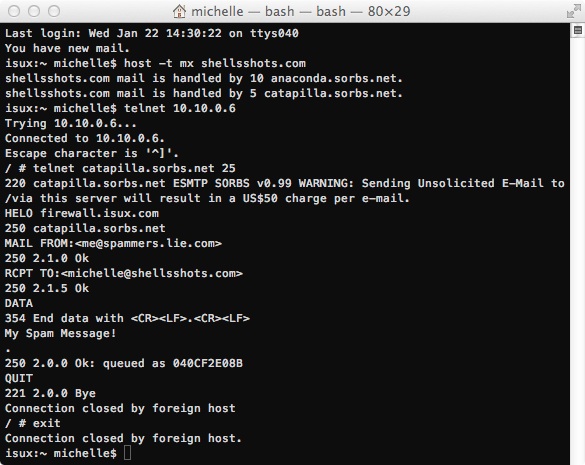
First the D-Link DNS-325 NAS…
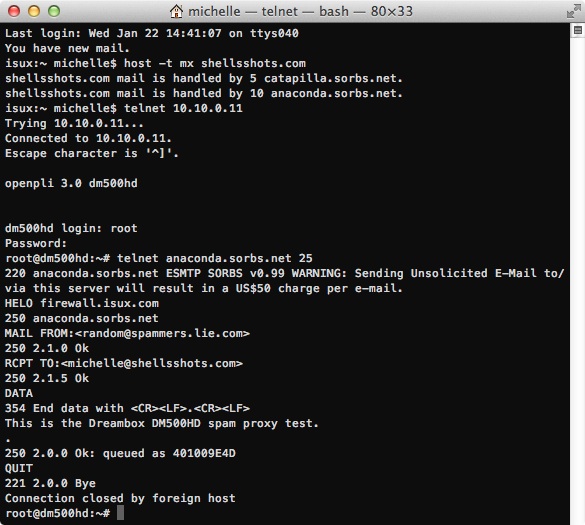
Now the Dreambox DM500HD (Remembering where the password is the default is ‘dreambox’ – which the malware “linux.darloz” is known to exploit):
The DM800 will work the same way, and in fact one could even install their own spamming program or proxy server using these set top boxes as this video will show:
Conclusion…
Until both manufacturers and end users understand the security risks of devices on the Internet any device is is an attack vector for spammers and hackers, and as that device may not be monitored you could have the FBI, NSA, Interpol or Australian Federal Police (or other law enforcement) come knocking on your door to arrest and jail you for something you know nothing about… Like trying to hack a nuclear reactor in Korea…
The final word…
I don’t have an Internet enabled fridge, and unless a manufacturer “donated” one to me I doubt I’ll ever have one (and no, I don’t need a new fridge, my Samsung 2009 side-by-side is perfect for my needs).. so no I can’t show you how to hack a fridge, just the same way I couldn’t show my employer. All I know is, “yup there is at least one out there that is hacked” it might not be the fridge is hacked, it might be another device sharing the connection, but the spamming host is showing an Internet enabled fridge when querying it… one can only draw conclusions.

